Why biometrics for authentication?
Biometrics are ideal for authentication because users don’t need to remember complicated passwords or carry additional tokens. Biometrics also prevent the sharing of authentication credentials, unlike passwords and other factors that aren’t uniquely linked to a person.
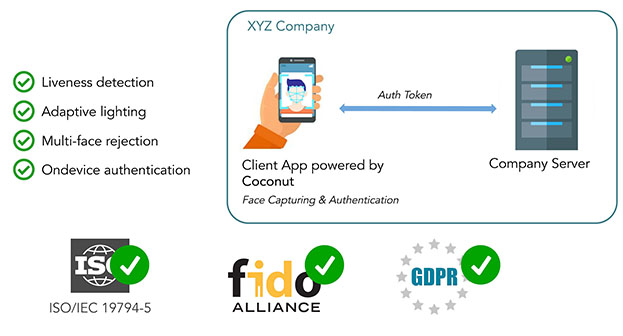
Coconut
Biometric Multi-Factor Authentication.
- Coconut is an award winning solution designed to be the perfect authentication solution and provide the best security for your data protection.
A product created with the vision of help make the world a better place. Overcoming the fear of losing any of your personal details, from any financial application you use. Coconut is a complete biometric enabled authentication and security platform that supports any financial application, that runs on any platform.
A state-of-the-art AI enabled multi-factor, multi-modal and multi-platform biometric authentication and security platform focused on meeting the needs of banking and financial organizations to protect their customer data. Coconut supports various biometric security factors such as Fingerprint, Iris, Voice, Face, Digital Signature and other generic security factors such as PIN, OTP, OCR and location. It is also ISO compliant, guarantees data protection and makes sure that no one can access any of your accounts without your permission.
A product created with the vision of help make the world a better place. Overcoming the fear of losing any of your personal details, from any financial application you use. Coconut is a complete biometric enabled authentication and security platform that supports any financial application, that runs on any platform.
Why mult-factor biometrics?
Each biometric has its own advantages and disadvantages for specific scenarios and use cases. Multi-biometric solutions are highly configurable and can greatly enhance flexibility; they allow different user convenience and security trade-offs to be made.
Key biometrics for consumer applications include:

Face
using a fingerprint capture sensor to authenticate a user based on the features of their fingerprint

Voice
using a microphone to capture a voice sample and authenticate a user based on their speech patterns

Fingerprint
using a fingerprint capture sensor to authenticate a user based on the features of their fingerprint

Iris
using a camera (with appropriate illumination), where an image of the iris portion of the eye (i.e., the colored portion)

Behavioral
using the behavior of a user to authenticate them, e.g., by analyzing keystroke dynamics (a person’s unique typing rhythm).

Palm
using a camera to capture an image of the palm and authenticate the user based on the lines of the palm's surface
